User Management
Overview
The factory default setting of the Cisco Nexus 3550-F Fusion (formerly ExaLINK Fusion) has one user defined, admin. Other users can be created which have limited permissions for monitoring etc.
A number of pre-defined roles are available on the Nexus 3550-F. These are:
guestmonitoruseroperatoradmin
The figure below depicts the capabilities of each role.
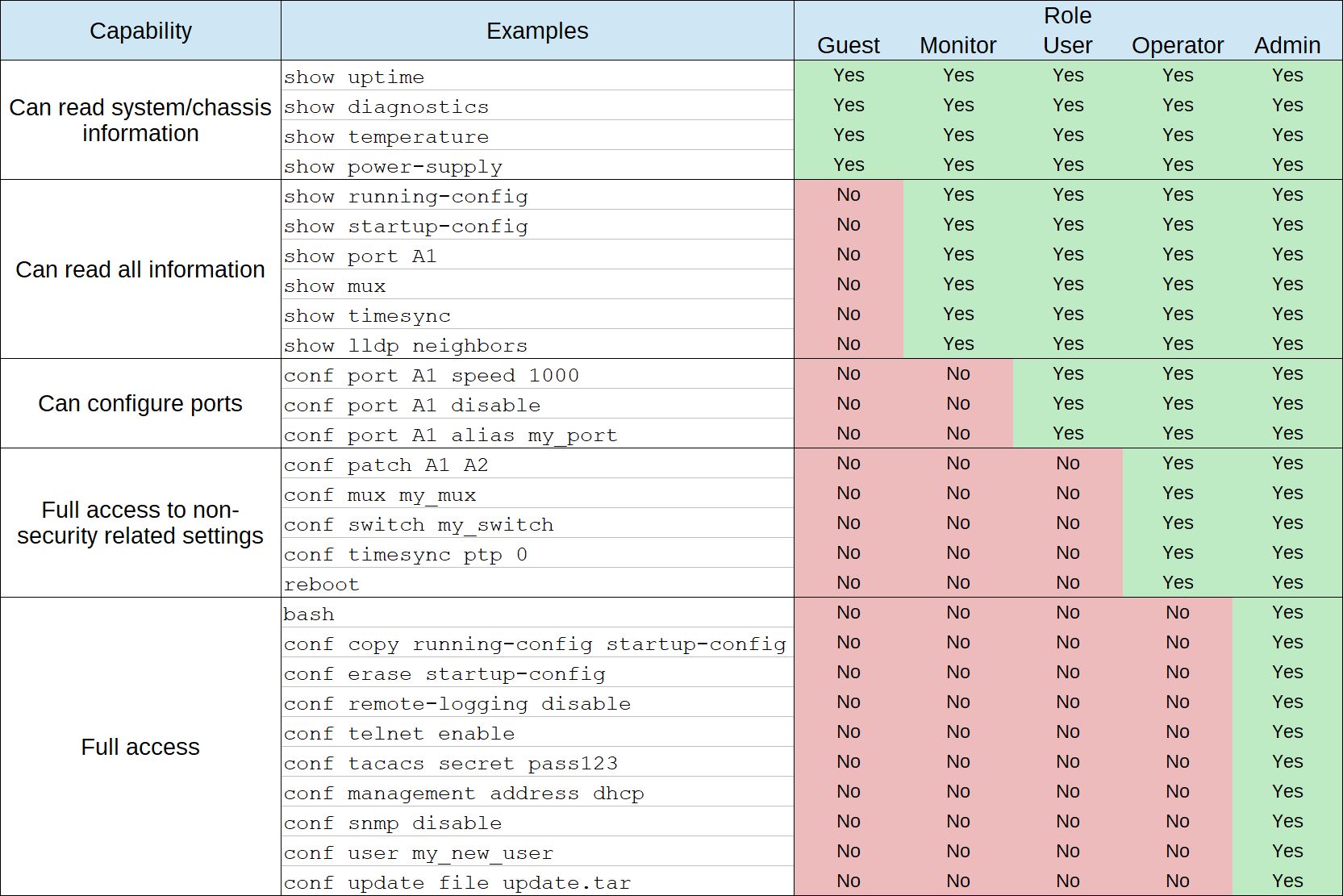
Note
The user editing described on this page relates to local users on the Nexus 3550-F being configured only. It is not possible to edit TACACS+ users on the Nexus 3550-F.
Also, when TACACS+ is enabled any locally defined users will not be able to login using their local credentials. Any local accounts that have the same username as an account on the TACACS+ server will take on roles/permissions as defined on the server.
Creating Users
Users are created using the user command, for example to create a new user
donald:
admin@N3550-F> config user donald
Creating new user "donald"
New password:
Re-enter new password:
Created new user "donald"
To delete a user, use the no user command with the user to be deleted, for
example:
admin@N3550-F> config no user donald
Deleted user "donald"
Note
The admin user cannot be deleted, nor can it have the admin role removed from it.
Changing Password
Any user with the admin role is able to change the password of any other user
using the password command, for example:
admin@N3550-F> configure user donald password
Changing password for user "donald"
New password:
Re-enter new password:
Password changed for user "donald"
Assigning Roles
Once a user has been created, a role should be added specifying the access this new user should have.
admin@N3550-F(config-user:donald)> role monitor
Added role "monitor" for user "donald"
Whilst it is possible to add multiple roles to a single user, the current
(fixed) set of possible roles means that there is no point in doing this. For
example if a user was assigned both the monitor and operator roles, as the
operator role is capable of performing all of the actions enabled by the
monitor role, adding monitor is unnecessary.
Roles can be removed using the no role form of the command, for example:
admin@N3550-F(config-user:donald)> no role monitor
Removed role "monitor" for user "donald"
Viewing Users
The list of users and each of their roles can be viewed using the show user
command:
admin@N3550-F> show user
Username Type Roles
-------- ----- -----------
admin local admin
donald local operator
fred local guest
jane local admin
SSH Keys
Users can add & remove an SSH key for themselves to facilitate authenticated logins without using a password. SSH keys can only be set/removed for the current user. To add a key:
admin@N3550-F(config-user:admin)> sshkey
Usage: sshkey <"ssh key">
Add a public ssh key for the selected local user.
admin@N3550-F(config-user:admin)> sshkey "ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAxTW4KRfzjiuEDu3thDRGrJeD5dwUDQdSYyeMy/8Yy/CMiRjl46kljhghe984LEBseE35kegiqtILi3bMuhYq2FY2v9d82tr0X7H/+o0Cbiq3GZz848O0wVK7BUF5gUDBUxMesAyjmWdDqOHlAgAOM+eamdowv7cEPo+4AO5RuJjEoJ77zD9Rtm1E560zkLG2P5ypGpXOJbg7AIdx/V11tKHbwPetdd6VPRGX5fe5/keIsgWv/vWYUIcCiN1B6o8P435tkkJJJj34988939488653XX21yONnmzPtF7ZFk4EZ+OW9GEaS3RHQaDV0hS59u2OTZMRHCQHAa+2MBn4GoQ== donald@duck.com"
Added ssh key for user "admin"
To remove a key, use the "no" form of the command:
admin@N3550-F(config-user:admin)> no sshkey "ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAxTW4KRfzjiuEDu3thDRGrJeD5dwUDQdSYyeMy/8Yy/CMiRjl46kljhghe984LEBseE35kegiqtILi3bMuhYq2FY2v9d82tr0X7H/+o0Cbiq3GZz848O0wVK7BUF5gUDBUxMesAyjmWdDqOHlAgAOM+eamdowv7cEPo+4AO5RuJjEoJ77zD9Rtm1E560zkLG2P5ypGpXOJbg7AIdx/V11tKHbwPetdd6VPRGX5fe5/keIsgWv/vWYUIcCiN1B6o8P435tkkJJJj34988939488653XX21yONnmzPtF7ZFk4EZ+OW9GEaS3RHQaDV0hS59u2OTZMRHCQHAa+2MBn4GoQ== donald@duck.com"
Removed ssh key for user "admin"
To see what SSH keys are added to a particular user, you can drop to the bash shell as follows:
admin@N3550-F> bash
ExaLINK Fusion shell
admin@N3550-F:~$ cat /home/admin/.ssh/authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAxTW4KRfzjiuEDu3thDRGrJeD5dwUDQdSYyeMy/8Yy/CMiRjl46kljhghe984LEBseE35kegiqtILi3bMuhYq2FY2v9d82tr0X7H/+o0Cbiq3GZz848O0wVK7BUF5gUDBUxMesAyjmWdDqOHlAgAOM+eamdowv7cEPo+4AO5RuJjEoJ77zD9Rtm1E560zkLG2P5ypGpXOJbg7AIdx/V11tKHbwPetdd6VPRGX5fe5/keIsgWv/vWYUIcCiN1B6o8P435tkkJJJj34988939488653XX21yONnmzPtF7ZFk4EZ+OW9GEaS3RHQaDV0hS59u2OTZMRHCQHAa+2MBn4GoQ== donald@duck.com
This page was last updated on Mar-08-2021.